It seems that password requirements are getting more intense. “Your password must be between 8 and 12 characters including at least one upper case letter, one lower case letter, one number, one special character, and no repeating characters. No passwords that you’ve used in the past 10 years. No words appearing in any dictionary. Passwords expire and must be changed monthly.”
This should come as no surprise. Digital security has been in the news often, with new data breaches, ransomware, and viruses reported on a nearly constant basis. The “common sense” solution is to make passwords increasingly complicated as a way to make it harder to guess. This has long been the guidance from the National Institute of Standards and Technology (NIST), which is the standard for those of us working under regulations like HIPAA and PCI.
And they’ve recently admitted that they’ve been wrong about passwords all along.
P4$$w0rd$ That Are Hard for Humans to Remember
These rules make it all but impossible for users to remember their passwords. At its core, it’s a usability issue. We’re making the process of authentication very difficult for the average person because, following that same logic, it should make it more difficult for criminals.
Unfortunately, what actually occurs is that users engage in a set of compensating behaviors such as writing passwords on sticky notes or using the same passwords for multiple accounts that ultimately make accounts less secure.
Just as importantly, these requirements make passwords only nominally more secure. As a security strategy, this type of complexity protects against the wrong attack scenario. In other words, the primary threat isn’t a TV sitcom scenario in which roommates try to guess your password. The more likely threat is a software program systematically trying combinations until it gets things right. This scenario becomes more and more likely as computers get faster.
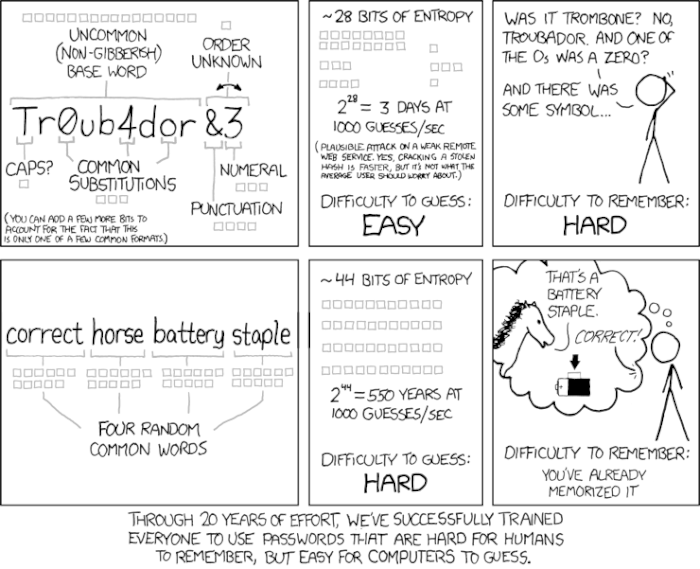
This difference is explained particularly well by geek comic XKCD.
New Guidelines on Digital Identity Released
All of this has lead NIST to issue a new set of recommendations as part of its updated Digital Identity Guidelines, released in June.
The guidelines are extensive, but here are some of the more meaningful new insights:
- Password length is more important than complexity.
- Remove requirements for complexity (upper/lower/numbers/spaces, etc.).
- Add a broader set of valid characters (emoji in your passwords, anyone?).
- Don’t auto-expire passwords.
Overall, the guidelines also embrace the notion that good user security requires a holistic approach, which means looking at how accounts are created, how passwords and account names are recovered when forgotten, how this information is stored, and how failed login attempts are handled.
What This Means for Developers
The guidelines encourage the hard work to fall on system developers rather than on users. To that end, there is a lot of guidance in the documents (some new, some existing) on how developers should put together systems that are less vulnerable to password-related attacks:
- Never display or email the clear-text password.
- One-way encrypt (a technique known as salting) passwords for storage. This prevents hackers from gaining access to passwords that they can use on other websites even if they do gain access to the database.
- Use lock out rules to limit the effectiveness of brute-force password guessing attacks.
- Don’t use a pre-determined set of challenge questions (or, if you do, make that list very long).
Looking forward, the guidelines encourage the use of risk-based adaptive techniques for authentication. In other words, make typical logins easy with the caveat that when something unusual is observed, make the user jump through additional security hoops. Higher risk scenarios might include logging in from a new computer, from a different country, or after a set of failed login attempts.
The Security of Your Content Management System (CMS)
If you manage your CMS in-house, take a moment to consider what the changes mean for your website security. If you work with a vendor, ask if they have plans to improve their security in light of these new recommendations.
At Geonetric, we develop software that is continually improving. Our product team keeps a watchful eye on industry trends, and we upgrade and update our CMS, VitalSite™ on a regular basis to provide new and improved functionality and security.
These changing security recommendations come at an opportune time as we’re launching a completely overhauled authentication and user management system for VitalSite, as well as our other applications. As we’re performing these upgrades it’s exciting to know that we can make life far easier for our clients by making their passwords less onerous, and at the same time, make them more secure.

